SCT Topic 6: Network Reconnaissance and OSINT
The initial phase of network security assessment is reconnaissance, in my understanding, this phase is used to gather the information of the target, including hosts, networks, users, services, etc.
It is an essential preparation mission before you can really do something to the target.
And the reconnaissance could be separated to passive or active.
Passive reconnaissance
In this case, "passive" means you do not directly interact or engage with target system. More specifically, you do not send any type of request to the target, thus the targets have no way of acknowledgement what you are doing.
You should use all the tools to gather more information as possible (free, open source, commercial tools)
- Querying Search Engines and Websites
- There are some typical data you can gather by querying search engines and websites
- Physical address of office locations
- Contact details, including email addresses and telephone numbers
- Details of internal email systems and routing
- DNS layout and naming conventions
- Files residing on publicly accessible servers
Here are some powerful tools we can use:
Google Advanced Search
It is very common for us to complain that Google returns some irrelevant results, but actually Google provides some powerful tools to enhance the search, it is the “Goolge Advanced search”, we can use its syntax to refine our search rules.
For example, “inurl:program” results in all the websites or resources whose url or cotent contains the keyword “program”, you can even use “allinurl:program” to query all the url which contains “program”.
Another common example is, when you search “program moon”, the result will probabaly give you a lot of results with “program” while excluding the keyword “moon” because obviously there is less result contains moon.
However, if you want to search the whole word which contains both “program moon”, you can surround the keywords with double quotes ““program moon””, so powerful, isn’t it?
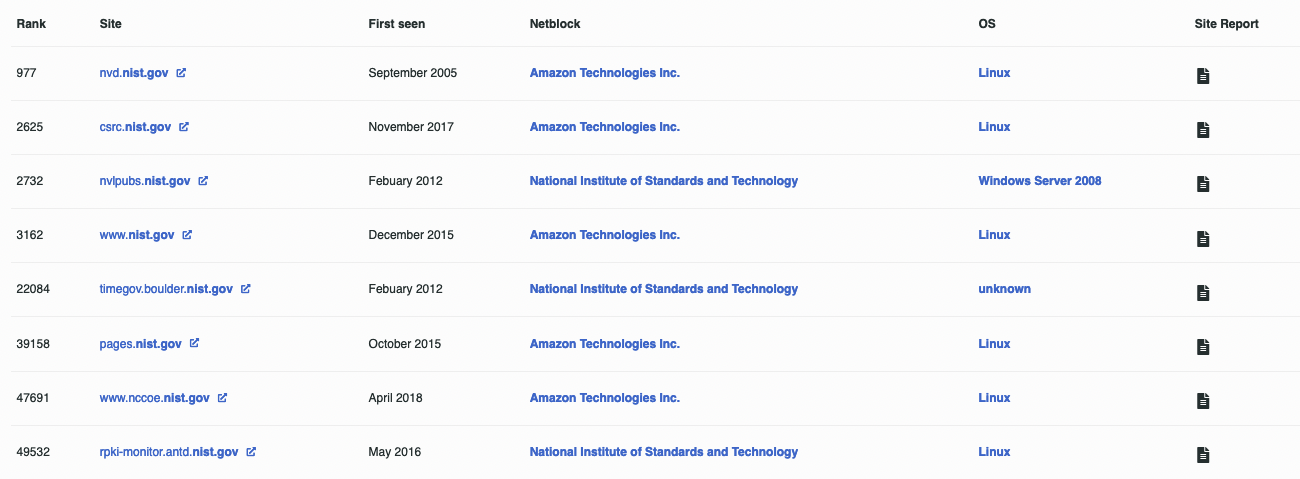
Querying Netcraft
The Netcraft Web Application contains historical server fingerprints, which you can use to check the OS versions or map network blocks of a company
The link above shows the result of all recorded NIST government sites with their site, netblock, OS.
Shodan
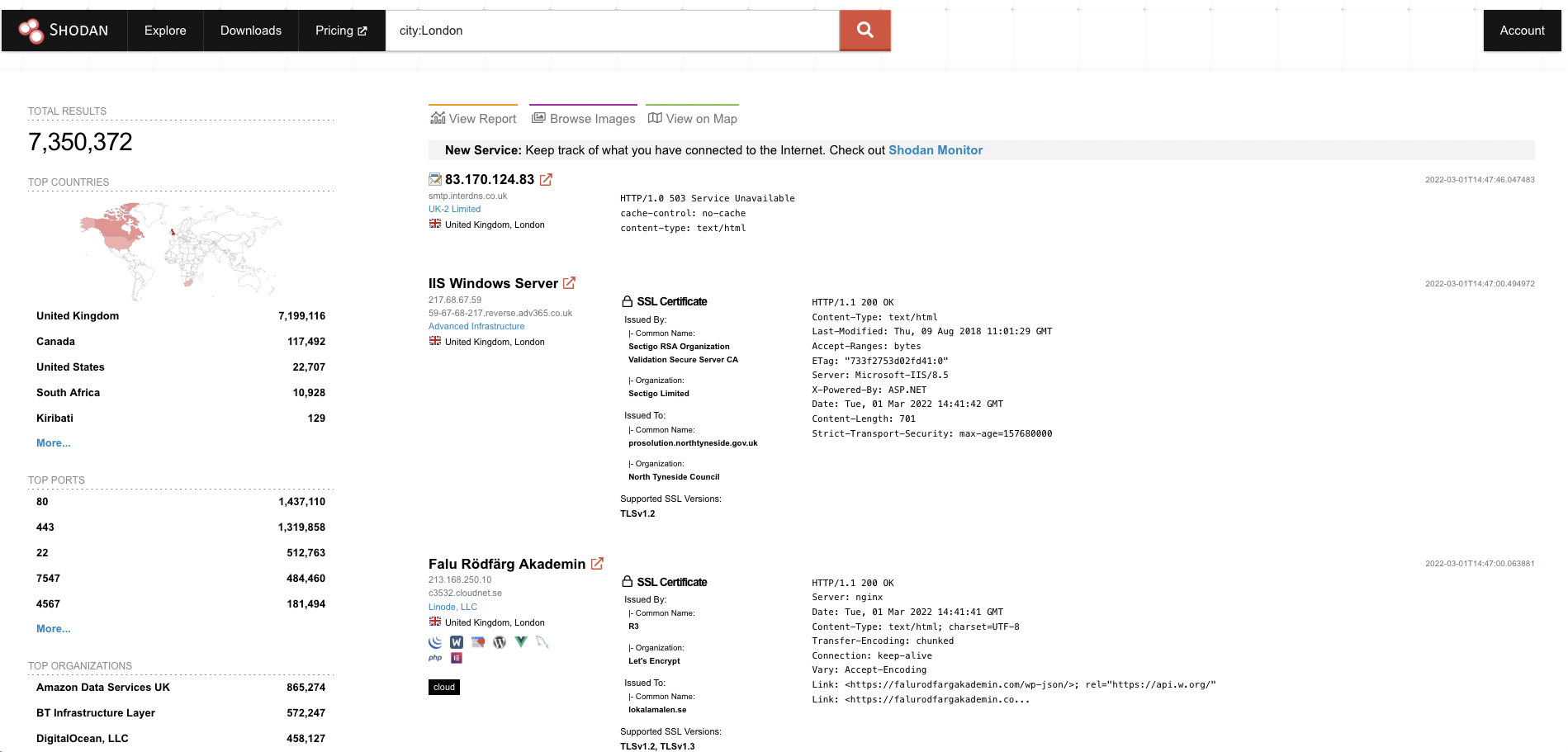
Shodan is a powerful search engine for gathering information on all devices connected to Internet.
Use search query syntax(city, country, http.title net, org, port, etc.) to search for the devices information within the whole Internet. Some entries even may list corresponding known vulnerabilities.
-
Differences with Google?
- Google queries the resources on
World Wide Web, but it is only a tiny fraction of Internet, Shodan’s goal is to provide a complete picture of the Internet. - Shodan explicitly requires search query syntax.
- Google queries the resources on
LinkedIn has a lot of personal profiles, it is always a good beginning for attacks like social engineering to dig deeper into an employee and an organisation. The LinkedIn Premium would help to look for people and roles without notifying them.
Domain WHOIS
WHOIS allows you to uncover the details information behind a domain. Typically, it contains:
- Administrative contact details
- Mailing addresses for office locations
- Details of authoritative name servers for each domain
Automated Email Enumeration
The TheHarvester tool is used for gathering information of emails, sub-domains, hosts, employee names, open ports, and banners from different public sources like search engines, PGP key servers, and SHODAN computer database.
example 1 Search email addresses from domain kali.org with results of 200 and using Bing as data source.
theharvester -d kali.org -l 200 -b bing
example 2
Search email addresses from domain nist.gov with results of 50 and using google as data source, finally saved the resources in myresults.html
DNS Querying
- What information we could retrieve from DNS Querying?
- Including:
Authoritative DNS server informationfromname server (NS) records- Domain and subdomain information
- Hostname information from A, PTR, and CNAME records
- Public points of presence that list mail exchanger (MX) records
In some cases, poorly configured DNS servers also allow you to enumerate:
Operating-system and platform informationof hosts from the host information (HINFO) record- Names and IP addresses of internal or nonpublic hosts and networks
- Why it is a passive recon?
- There is no active scanning or probing of the target networks, you just probe and query the information with authoritative DNS servers (for those domains or network blocks that are often run by ISPs).
Meanwhile, most name servers are not aware of these potential sweeps, because they looks like normal DNS traffic.
-
Forward DNS Querying
Legitimate forward query:
- An end user accesses web site
- During the receipt of email when SMTP mail exchanger information is requested about the relevant domains
Attacker: Issue forward DNS queries to identify mail servers and other obvious Internet-based systems
Tools:
- The Sam Spade Windows client (available from http://www.samspade.org)
- The nslookup client found within most operating systems
- The host client found within Unix environments
- The dig client found within Unix environments
-
DNS Zone transfer Techniques
DNS zone : A DNS zone file contains all the naming information that the name server stores regarding a specific DNS domain, often including details of nonpublic internal networks and other userful information you can use to build an accurate map of the target infrastructure.
Why we need DNS Zone transfer? : In most organisations, they use multiple name server to implement load balancing and fault tolerance.
The main name server is known as the `primary name server` and all subsequent name servers are `secondary name servers`. Either a `primary` or `secondary` name server can be <span class="underline">queried for name resolution</span>, thus, it is important that each name server have current (primary) DNS zone information. To ensure this, a `secondary name server` will <span class="underline">regularly</span> requests a complete listing of the computers it is responsible for from the primary.Tools used to request DNS zone transfer information include:
- The Sam Spade Windows client (available from http://www.samspade.org)
- The nslookup client found within most operating systems
- The host client found within Unix-based environments
- The dig client found within Unix-based environments
-
Reverse DNS Sweeping
You may notice in previous techniques, they require domain name as parameter, but in this case, we do the opposite thing against name resolution, we called
reverse DNS.It can gather details of hosts that may be protected or filtered but still have DNS hostnames assigned to them. It is also able to identify hosts and potential weaknesses within Internet-based points of presence because it reveals hosts and networks that may not be revealed during DNS zone transfer queries.
Countermeasures
- Disable directory indexing on Web servers
- Use “robots.txt” to prevent indexing of certain content by search engines but do NOT rely on it to protect sensitive data
- Use generic details in WHOIS data (or privacy-protect it)
- Disable DNS zone transfers to untrusted hosts
- Prune DNS zone files from unnecessary information
- Preventing TypoSquatting: you may check if a similar domain is available, if you are Nintendo you may check for alternative domains with small variants (that people may mistype by accident while trying to visit your website).
Active reconnaissance
Compare to the passive reconnaissance, ACTIVE means actively interact with target services, network and hosts.
Active Reconnaissance Tools
Nmap (“Network mapper”) is the most used tools to perform Internet network scans, is a free and open source utility for network discovery and security auditing.
Other commonly used tools include:
- Nessus
- Rapid7 Nexpose
- QualysGuard
You always need to use both free and commercial tools to assess the network because the attackers will do the same!
Some types of nmap scans
- TCP scanning with connection (-sT, the default), Connection scans
- TCP scanning with SYN packets (-sS)
- TCP scanning through FIN (finished, is used to initial to close the connection) packets (-sF), no log file on server
- TCP scanning empty (-sN)
- TCP scanning Xmas Tree (FIN + PUSH + URG, -sX)
- TCP scanning through ACK packets (-sA)
- TCP canning with Window Size (-sW)
- TCP scanning through R
nmap 10.130.1.43
- nmap -Sp
- The -sP option sends an ICMP echo request, TCP SYN to port 443, TCP ACK to port 80, and an ICMP timestamp request by default.
Host Scanning
- Aim
- To confirm if a target IP is reachable/active through Internet
Automated execution of a series of ping commands to determine which systems are active
Known Techniques
-
Ping sweep
-
ICMP sweep
-
Normally, the
"ping"command is used to sendICMP ECHO_REQUESTpacket to expectICMP ECHO_REPLYHowever, it takes too much time in a large-scale networks because of waiting for the replay sequencly
Thus, we could use fping to sends “blocks of ping” at the same time to fix this problem
- Defense against ping and fping scans
- Block all ICMP traffic
- Counter-defense
- scan ports at the transfer layer (TCP/UDP), e.g., through
nmaporhping3to send TCP ACK, you can see an example in Idle scanning later.
- scan ports at the transfer layer (TCP/UDP), e.g., through
Port Scanning
- Aim
- Try to connect to TCP and UDP ports of the target system to determine which network services are active (or LISTENING).
nmap -p(range) <target IP> namp -p3389,20-100 10.130.1.43
It is important to know the active ports which can by exploited to attack.
- UDP Portscan
- Send a zero-length UDP packet to each port to determine which UDP services are available, if an
ICMP error message“port unreachable” is received, it assumed that this service is unavailable.nmap -sU 192.168.1.1 - TCP Portscan
- Try to establish a TCP handshake to all the 65535 ports of the victim host to determine TCP services are available or not:
-
Advantage: no need to be root
-
Disadvantage: very noisy
nmap -sT 192.168.1.1
-
-
TCP FIN Scan
The attacker sends a FIN-marked (to close TCP connection) packet to victim host
- If the port is closed, a
RST packetis sent back - If the port is open, the
FIN packetis ignored (timeout)
nmap -sF 110.130.1.43 - If the port is closed, a
-
Idle Scanning
https://www.icterra.com/what-is-idle-scan/
How to understand the word “idle”? :
"Idle"is the requirement of the zombie computer, it requires the zombie computer have low network traffic (or better it has almost no traffic). Thus it usually happens overnight.So why we need the zombie computers do not have any other traffic?
The reason is directly pointing to the mechanism of
idle scanning: basically, idle scanning aims to use zombie computers to “relay” the scan without exposing attackers to victims, and get the status of service ports.Before we elaborate the mechanisms of idle scanning, let’s briefly recap the knowledge about the response of SYN segments
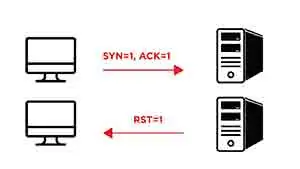
TCP SYN Scanning: AKA “half-open” scanning
- If a
SYN/ACKsegment is sent to a host, it will respond withRST(reset)segment (because there is no corresponding session which started with aSYNearlier toSYN/ACK) - If a
SYNsegment is sent to a host, it will respond with aRST(reset)if the port closed
-
If a
SYNsegment is sent to a host, it will respond with a RST if the port closed,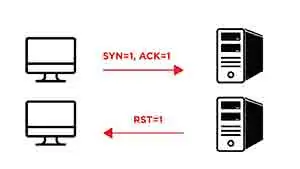
-
If a
SYNsegment is sent to a host, it doesn’t give a response if the port filtered.
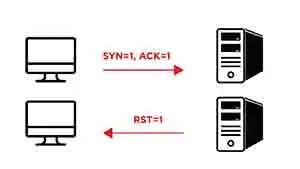
Now let’s talk about the mechanism details with three scanning examples:
-
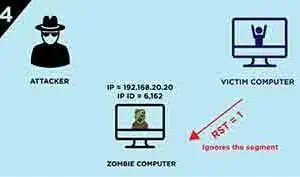
Idle Scan (Victim Port Open)
-
The attacker sends a
SYN/ACKsegment to the Zombie computer -
Zombie computer responses with
RSTsegment with itsIP IDis incremented by “one” -
Since attackers get the initial IP ID value of Zombie computer, they will then sends a spoofed
SYNsegment with Zombie computer’s IP address to the Victim’s computerThe Attacker pretend to be zombie computer, and communicate with the victim.
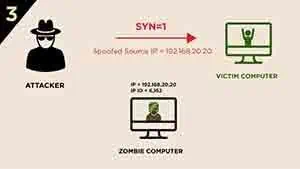
-
Since the target port is open, the victim computer will response a
SYN/ACKsegment to Zombie computer.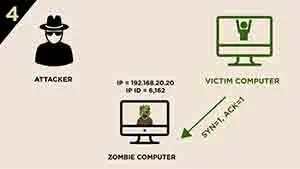
-
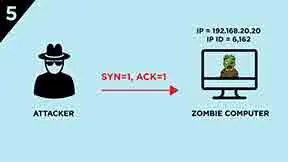
However, the zombie computer did not establish a session with Victim computer, so when it receive the
SYN/ACKsegment, it will respond with aRSTsegment to it, and meanwhile, increases itsIP IDby “one” to 6,163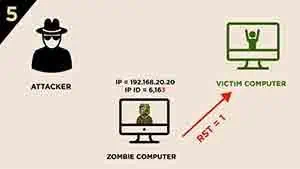
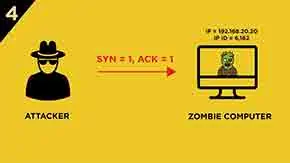
-
The attackers want to check the current
IP ID, thus they send anotherSYN/ACKsegment to The Zombie computer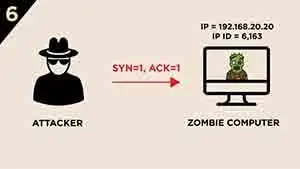
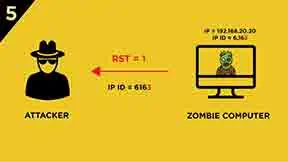
-
The Zombie computer responds with a
RSTsegment and increases itsIP IDby “one” to 6,164 then sends to the attackerThe attackers check the IP ID is increased by “two” which could confirm that the victim computer is OPEN.
Based on this, we can also get the reason why we require the victim computer to be “idle”, otherwise, the increment could be uncertain.
-
-
Idle Scan (Victim Port Closed)
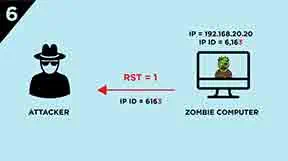
So, what if the port is closed? This time, the spoofed
SYNsegment will not get the response ofRST, which avoid the Zombie computer to interact with Victim computer, and theIP IDdid not increase, thus finally we will get theIP IDonly increase by “one”, which indicate the port is closed.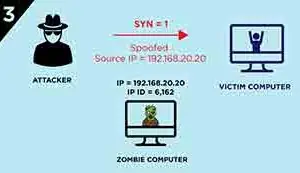
-
Idle Scan (Victim Port Fillterd)
If there is a firewall filter the spoofed
SYNsegment, the Victim computer will not send anything to Zombie computer, which result in the sameIP IDas Port closed case.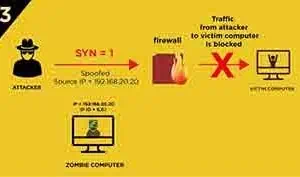
- If a
OS Fingerprinting
- Aim
- To determine the operating system of a host: Which OS? Which Version?
sudo nmap -O localhost
#+begin_src bash nmap -O -PN 192.168.1.1/24 k#+end_src
Service Enumeration/Banner Grabbing
By grabbing the headers of exposed services, nmap (option -sV) can try to infer the exact service version
Nmap Scripting Engine
Nmap provide a series of scripts for checking the vulnerabilities based on open services of victim host
Scripts can be found in usr/share/nmap/scripts
nmap --secript [script name] [target]
Mitnick-Shimomura attack
IP spoofing attack
We assume A and B trust each other, they will establish connection without further authentication with each other.
And C is the attacker who want to impersonate B with respect to A in opening a TCP connection
- C first kill B with flooding, crashing or redirecting, then B can’t send RST segments back to A
- C sends a spoofed TCP SYN segment with B’s IP address to A, and s_c as the sequence number
- A replies with a TCP SYN/ACK segment to B with s_s as the sequence number. But B can’t reply.
- C does not receive segment from A, but C wants to continue the connection, so C send an
ACKsegment with s_s + 1 as the acknowledgement number- C need to guess the sequence number
Countermeasure:
- Block scanning (e.g., ICMP)
- Check open ports and configuration, to make sure that only appropriate services are exposed.
- Monitor network activity (e.g., Intrusion Detection System, SIEM)