CFC Week 7: Memory and network forensics
Learning outcomes
- Define the fundamental aspects of computer and network forensics.
- Describe the data collection processes through the different abstraction layers.
- List the kind of evidence that can be obtained from volatile memory and non-persistent network data.
Device forensics
target the OS and the data structures present in the system
What are primary sources of evidence in device forensics?
are storage devices:
- Hard disk drives (HDDs)
- Solid state drives (SSDs)
- External media (USB sticks)
How to understand the data stored on devices?
Use Data abstraction layers:
-
Physical media : - lowest level examinations
- Access through host bus adapter (HBA) interface
- which implement low-level operations: SATA and SCSI
-
Block devices : block device is an abstract device of fixed size block
use term sector as unites for magnetic hard disks
Data acquisition at the block level is done through imaging
-
File system : aims to organise the block storage into a file-based store
provide files with attributes (name, size, owner, timestamps, access permissions, etc.)
-
Application artefacts : where we find executable binaries, libraries, configuration and log files and registry entries
What is the physical data acquisition in device forensics?
is the process of obtaining data directly from hardware media,
without the mediation of any potentially untrusted third-party software
we also use logical data acquisitions which relies on one or more software layers as intermediaries
Characteristics of SSDs
SSDs use semiconductors to store data
two memory areas:
- one area is used to save data
- one area is used as a cache
SSD blocks need to be written twice in order to be reused:
- First write to reset the state
- Second write to store the data
File content carving
aims to recover the data by reassembling file contents from fragments
why this works? Most file formats have specific beginning and end tags
Four types of file content, require different carving approaches:
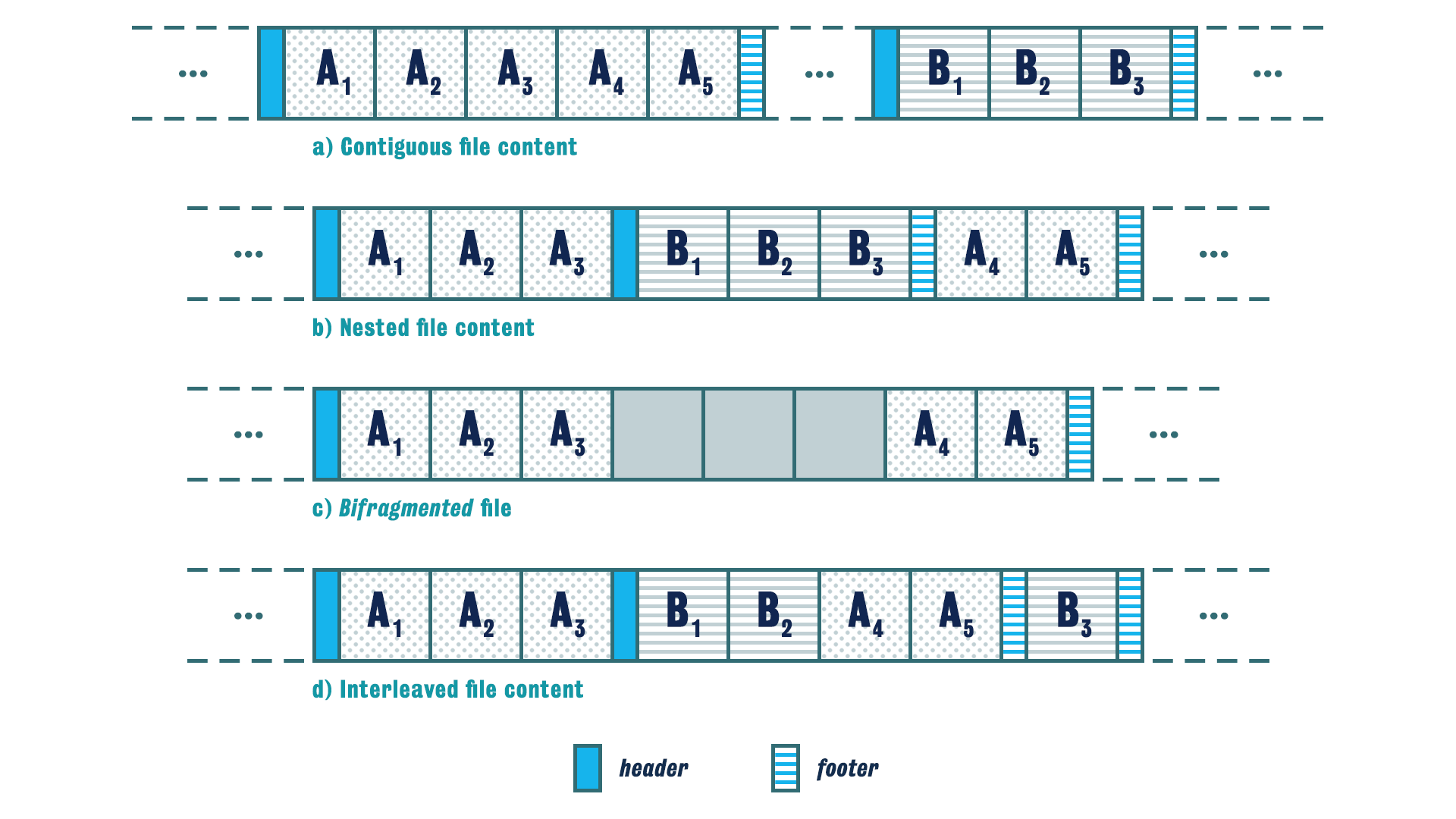
-
Contiguous : The header of file A is followed by the contents of file A and ends with a footer of that file
-
Nested : The header of file A is followed by a part of that file’s content, then the header of file B is present followed by the content and footer of that file. A finished after B.
-
Bifragmented : The Header and some part of file A followed by some unrealted data then followed by remains
The recovery of this file will depend on how easily the unrealted data is recognised
-
Interleaved : The content of file A is mixed with File B, A finished before B
Why we are interested in doing Memory forensics?
Data can persist for quite a long time in volatile memory Volatile memory can contain useful information which hard disk does not (en/decryption key)
How to perform offline memory forensics
Freeze the RAM of a computer
What a forensic analyst must know about memory forensics?
- What are the things that might change across time?
- What are the things that will not?
- How presenting evidence from memory can impact your investigation
What are the challenges behind live forensics?
- In live forensics, we’re unsure whether evidence will be accepted or not.
- Extract evidence from memory is not easy and takes long time
What does generally change?
- Process information
- identifying correlated user actions and file system activities, potentially demonstrating their intent
- Running processes
- Threads and loaded systems modules
- Copy of the individual processes’ code, stack, heap, code and data segments
- Artefacts and fragments
- Caching disk and network data tends to leave traces in memory for a long time
- File information
- open files
- shared libraries
- shared memory
- anonymously mapped memory
- Network connections
- closed network connections
- protocol information
- sending and receiving queues of data not yet send or delivered
Network forensics
monitor and analyse the computer network traffic for information gathering, legal evidence or intrusion detection
Why is the difference between network forensics with other digital forensics
-
network investigations focus on volatile and dynamic information
-
because network traffic is transmitted and then lost
-
Thus the data would be actively collected
What are two common scenarios in network forensics?
- Security
- monitor a network for anomalous traffic and identify intrusion.
- when attacker has erased all log files on a compromised host
- Law enforcement
- reassemble transferred files
- search for keywords
- parse human communication
What are two strategies in network forensics?
- “catch-it-as-you-can”
- all packets are captured and written to storage for analysis
- require large amounts of storage
- “stop, look, listen”
- each packet is analysed in a rudimentary way in memory
- only certain meta information is saved
- require more processing capabilities
What method we apply to network forensics on ethernet layer?
Use sniffer to eavedrop the beta stream: Wireshark and tcpdump
Wireless forensics
collect and analyse wireless network traffic that can correspond to plain data or with a broad usage of.